We Guarantee Your Security
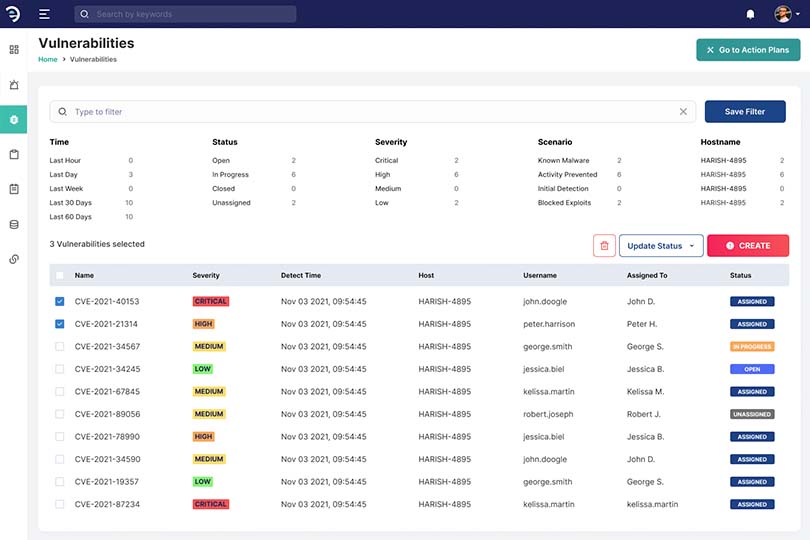
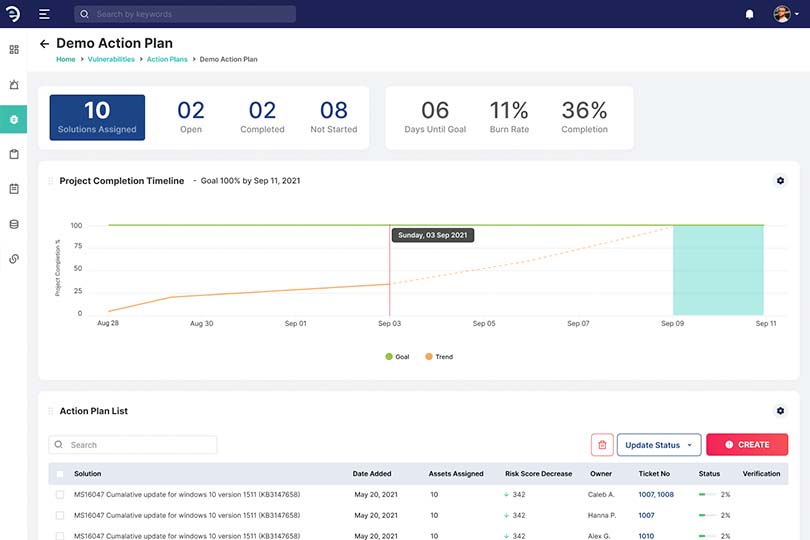
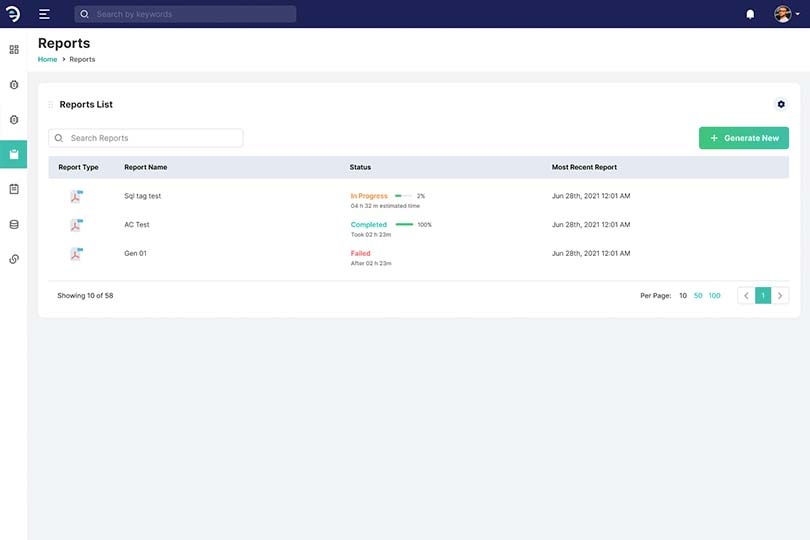
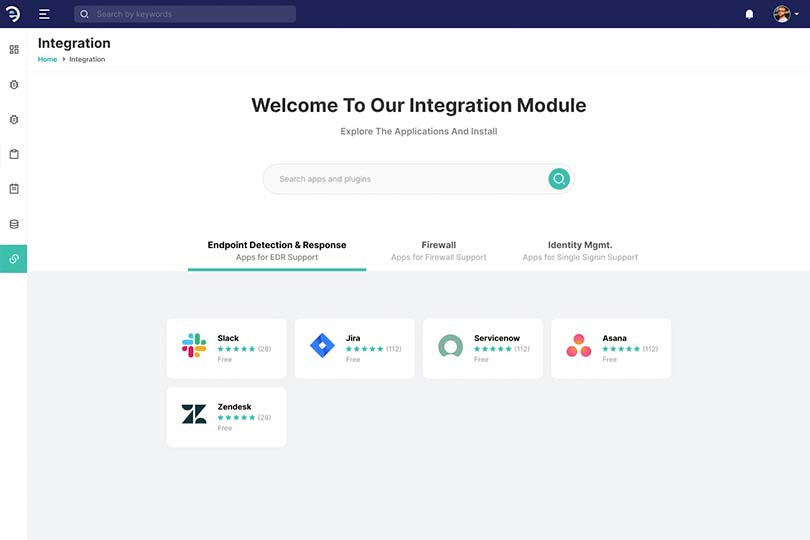
Our platform is equipped with real time monitoring, threat hunting and anomalous reporting with AI supportOur network security model, based on a strict identity verification process. The framework dictates that only authenticated and authorised users and devices can access applications and data. At the same time, it protects those applications and users from advanced threats on the internet.